Closed Systems and Open Systems
In 21 CFR Part 11 and the ER/ES Guidance (Japan’s guidance on electronic records and electronic signatures for pharmaceutical applications), the terms “closed system” and “open system” are defined. The author has observed that there are many cases where the differences between these systems are not properly understood.
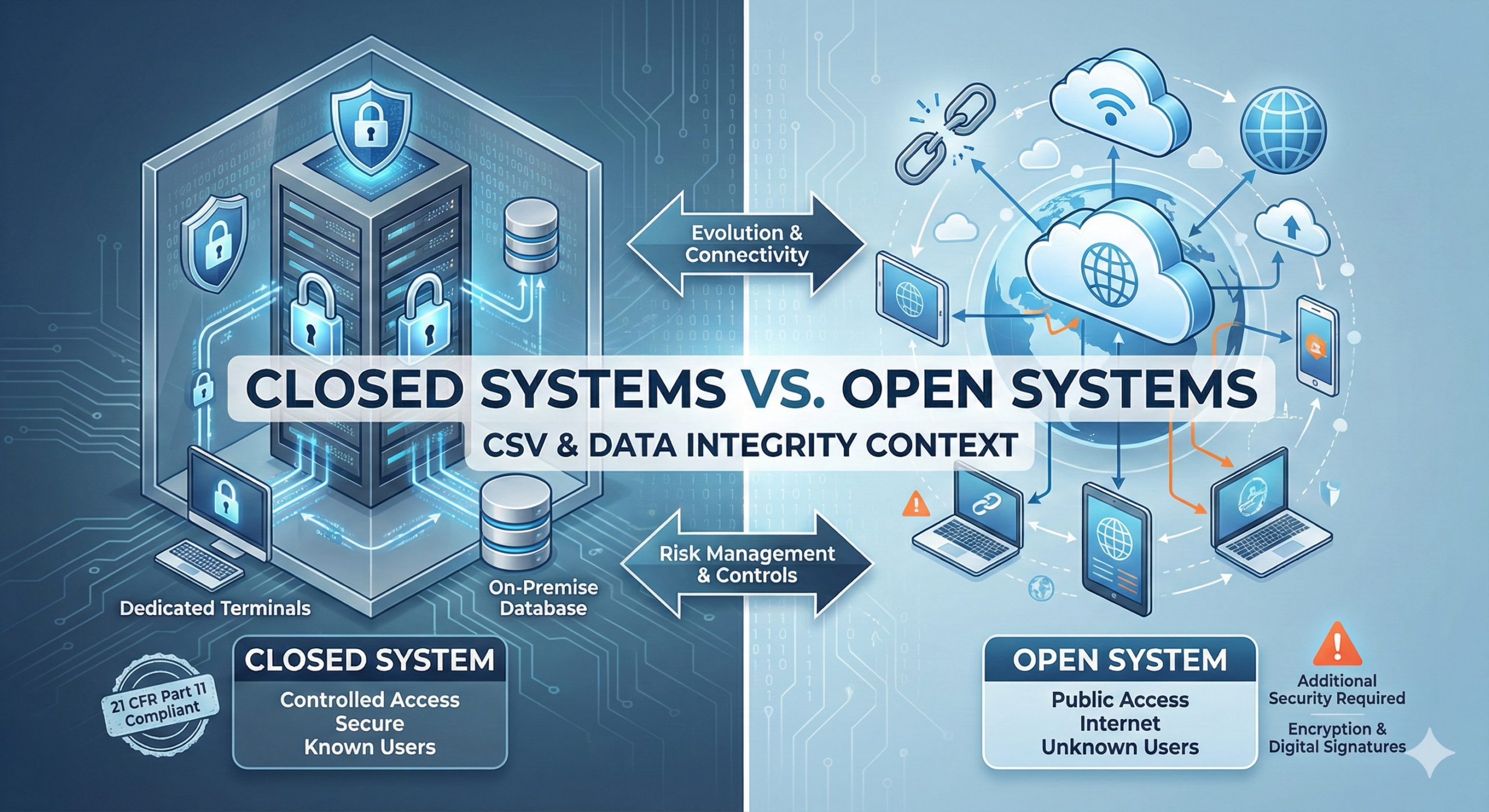
In 21 CFR Part 11, closed systems and open systems are defined as follows:
Closed System: An environment in which system access is controlled by persons who are responsible for the content of electronic records that are on the system.
Open System: An environment in which system access is not controlled by persons who are responsible for the content of electronic records that are on the system.
These definitions may seem unclear at first glance. To put it more practically, a closed system refers to computer systems within a company’s premises, including those connected via a Local Area Network (LAN). An open system refers to systems that handle communications over the Internet or other networks where access control cannot be fully maintained by the responsible parties.
Under normal circumstances, open systems do not exist in isolation. An open system emerges when a closed system within a company is connected via the Internet to another closed system in a different location. For example, when your home PC connects to Amazon or Rakuten servers, this creates an open system scenario.
In open systems, there are servers on the network that cannot be managed or controlled by your own company (or yourself). Therefore, the Internet presents risks such as eavesdropping, tampering, and impersonation. To mitigate these risks, open systems require the use of encrypted communications and digital signatures. Specifically, using TLS (Transport Layer Security) – the successor to SSL (Secure Socket Layer) – satisfies these requirements.
Current Regulatory Landscape
In recent years, encrypted communication has become mandatory for all Internet traffic. Since October 2018, websites without HTTPS implementation display warnings such as “Not Secure” in virtually all modern browsers. This trend has accelerated, and as of 2026, TLS 1.2 or higher is the minimum standard, with TLS 1.3 increasingly becoming the norm. Older protocols such as SSL 3.0, TLS 1.0, and TLS 1.1 are now deprecated and should not be used due to known security vulnerabilities.
Important Considerations for Pharmaceutical and Life Sciences
When implementing electronic records and electronic signatures in regulated environments, organizations must consider:
Access Control: Closed systems require robust user authentication and authorization mechanisms to ensure only authorized personnel can access and modify electronic records.
Audit Trails: Both closed and open systems must maintain complete, computer-generated, time-stamped audit trails to independently record operator actions.
Data Integrity: Following the ALCOA+ principles (Attributable, Legible, Contemporaneous, Original, Accurate, plus Complete, Consistent, Enduring, and Available), data integrity must be maintained throughout the data lifecycle.
Cloud-Based Systems: Modern cloud services (such as SaaS applications) present unique challenges. While the cloud provider’s infrastructure may be secured, the connection over the Internet typically classifies these as open systems, requiring appropriate encryption and digital signature capabilities.
Vendor Management: For open systems, organizations must ensure service providers and vendors implement appropriate security controls and maintain GxP compliance where applicable.
Digital Signatures in Open Systems
According to 21 CFR Part 11, when electronic signatures are used in open systems, they must be based on digital signatures. Digital signatures provide:
- Authentication: Verification of the signer’s identity
- Integrity: Assurance that the signed data has not been altered
- Non-repudiation: The signer cannot deny having signed the document
These requirements ensure the trustworthiness and legal validity of electronic records transmitted over networks where complete access control cannot be guaranteed.
System Classification Summary
| System Type | Access Control | Network Environment | Security Requirements | Typical Examples |
| Closed System | Controlled by responsible persons | Internal network (LAN) or isolated environment | User authentication, authorization, audit trails | In-house LIMS, internal databases, standalone systems |
| Open System | Not fully controlled by responsible persons | Internet or networks with external access points | Encrypted communications (TLS 1.2+), digital signatures, enhanced authentication | Cloud-based applications, web portals, remote access systems, EDC systems |
Practical Implementation
For organizations implementing computerized systems in regulated environments, the distinction between closed and open systems has direct implications for validation, security controls, and compliance documentation. System owners must carefully assess their system architecture and network topology to correctly classify their systems and apply appropriate controls accordingly.
The evolution of technology continues to blur traditional boundaries between closed and open systems. Hybrid approaches, such as Virtual Private Networks (VPNs), cloud services with dedicated connections, and zero-trust architectures, require careful evaluation to ensure they meet regulatory requirements while leveraging modern technological capabilities. Organizations should work closely with quality assurance, IT security, and regulatory affairs teams to ensure proper implementation and ongoing compliance.

Comment